Innovations in the user identity management space have been a trend in the past couple of years. Most of these developments across business and technology fronts have been around identity management in cloud computing, enabling the authentication and authorization processes right in the cloud.
The primary goal of identity management in cloud computing is dealing with personal identity information so that a user’s access to data, computer resources, applications, and services is controlled accurately.
What is Cloud Identity Management

Identity management in cloud computing is the subsequent step of identity and access management (IAM) solutions. However, it is a lot more than merely a straightforward web app single sign-on (SSO) solution. This next generation of IAM solution is a holistic move of the identity provider right to the cloud.
Known as Directory-as-a-Service (DaaS), this particular service is the advanced version of the conventional and on-premises solutions, including Lightweight Directory Access Protocol (LDAP) as well as Microsoft Active Directory (AD).
Features of a Modern Cloud Identity Management Solution
The following are a few advantages of identity management in cloud computing:
- It offers a consistent access control interface: Applicable for all cloud platform services; Cloud IAM solutions provide a clean and single access control interface.
- It offers superior security levels: If needed, we can easily define increased security levels for crucial applications.
- It lets businesses access resources at diverse levels: Businesses can define roles and grant permissions to explicit users for accessing resources at diverse granularity levels.
Why Do You Need Cloud IAM
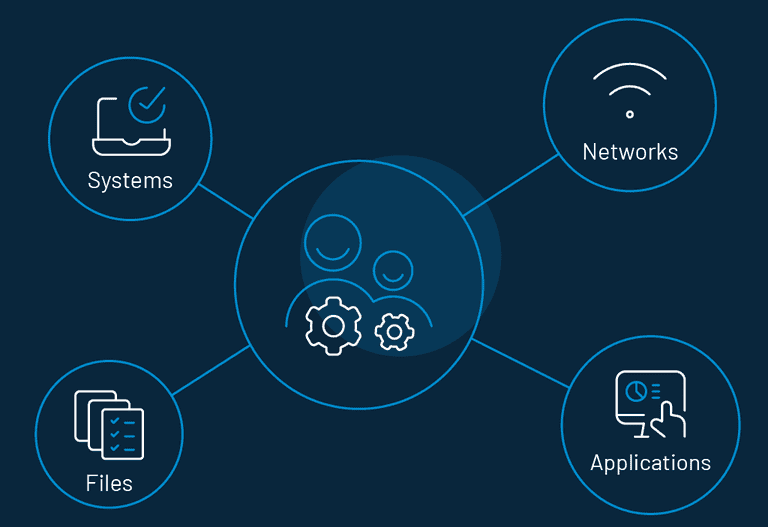
Identity management in cloud computing incorporates all categories of user-base who can operate in diverse scenarios and with specific devices.
A modern cloud Identity and Access Management (IAM) solution helps to:
- Connect professionals, employees, IT applications, and devices securely either on-premise or the cloud and through involved networks.
- It makes it easy to share the network abilities with the entire grid of users who were precisely connected with it.
- It offers zero management overhead, enhanced security levels, and easy management of diverse users with directory service in a SaaS solution.
- It is utterly known that cloud-based services are enabled, configured, and hosted by external providers. This scenario may also get the least hassle, either for users or clients. As a result, many organizations can enhance their productivity with cloud IAM.
- SaaS protocol is created and used as a hub for connecting with all virtual networks of distributors, suppliers, and partners.
- Business users can deal with all services and programs in one place with cloud services, and Identity management can be enabled with a click on a single dashboard.
- Easily connect your cloud servers, which are virtually hosted at Google Cloud, AWS, or elsewhere right next to your current LDAP or AD user store.
- Widen and extend your present LDAP or AD directory right to the cloud.
- Deal with Linux, Windows, and Mac desktops, laptops, and servers established at different locations.
- Connect different users to diverse applications that use LDAP or SAML-based authentication.
- Effortlessly handle user access controls to WiFi networks securely by using a cloud RADIUS service.
- Enable GPO-like functionalities across diverse Windows, Mac, and Linux devices.
- Facilitate both system-based as well as application-level multi-factor authentications (2FA).
These abilities help build a platform that connects users to virtually all IT resources through any provider, protocol, platform, or location.
IT admins know that legacy identity management systems (in most cases) struggle when they are matched to cloud services and the likes of AWS.
So, the newest approach to identity management in cloud computing extends your current directory to the cloud with a commanding, easy-to-use SaaS-based solution.
Introducing Loginradius Cloud IAM - Implemented Across Markets by Industry Leaders
LoginRadius enables businesses to provide an enhanced consumer experience and protects the managed identities. Utilizing the CIAM platform, organizations can offer a streamlined login process, registration, password setup, along with safeguarding consumer accounts and complying with precise data privacy regulations.
LoginRadius enables this by providing open-source SDKs, integrations with more than 150 third-party applications, pre-designed and personalized login interfaces, and superior security products such as RBA, MFA, and Advanced Password Policies. More than 3,000 businesses appreciate the platform with monthly reachability of 1.17 billion users globally.
Compared to conventional deployments with on-premise servers, LoginRadius facilitates everything for its customers, including upgrades, maintenance, data and infrastructure management, security, compliance, and complete privacy with 24/7 technical support.
The LoginRadius identity platform increases the value of businesses by integrating with hundreds of third-party tools. The cloud directory offers everything an engineering team requires to manage consumer data. It enables you to tailor the abilities as needed. However, the platform is API driven, meaning it is easily accessible by developers.
Further, when consumer data is completely locked away across silos, businesses will face multiple challenges. LoginRadius offers integrations to take apart data silos and the challenges that come with them.
The cloud identity platform completely complies with precise privacy regulations and makes things simpler by giving consumer control when the data is entirely centralized.
Conclusion
Identity management in cloud computing is highly critical to your organization. It can persuade the productivity of your employees and the security of your organization. It can also have immense control over what technology solutions you select.
However, IAM solutions have to be supple across identity management and access control in cloud computing to match the current complexities of the computing environment.
If you are locked into some conventional platforms or service providers because of your active directory ad service, explore a vendor-neutral cloud identity management solution.